How censorship-proof is Nostr?

This news was shared in recent days by Efrat Fenigson, Israeli Bitcoin activist and podcaster of “You’re the voice” with a blog on Substack https://substack.com/@efrat
https://blossom.primal.net/6bffaa4ba1ca21ac2681a839ae852e84a3099bacdfd1ff48d10701b8e6d6274a.mp4
According to her own statement, she was on vacation in Australia when she was denied access to Substack because she was not willing to perform a KYC (age verification). This did not change even after she traveled on to Indonesia, although the regulation is only legally binding in Australia. Even using a VPN did not help her. This access restriction presumably also applies to all Australian readers or users whom Substack considers to be Australian.
Efrat Fenigson is also active on Nostr with the profile efrat@primal.net, where she was able to continue publishing without restrictions and was accessible to her community. Of course, the question immediately arises as to why she does not also have her blog on Nostr. So far, only short messages, pictures, and videos from her can be found there. And in times of increasingly rigid censorship measures, how is her content protected against any kind of usage restrictions? Let’s play through the situation using this example, from the perspectives of content creator and consumer.
Access
Authors have unrestricted access to their assets in Nostr as long as they have the key (nsec) to their profile. Even the unavailability of individual apps or services does not restrict this, as numerous alternatives are available. Users do not even need a Nostr profile (key) if they only intend to read and not interact.
https://primal.net/efrat
https://iris.to/npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz
https://pareto.space/p/npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz
Identitity (Profile)
The above URLs demonstrate the intentional redundancy in information access, but at the same time also a potential weakness in terms of identity and findability (the npub from examples 2 and 3 is difficult to remember). Ms. Fenigson has decided to have her Nostr name (NIP-05) managed by Primal. If it is no longer available there (and there are many reasons why this could happen), her visibility will be severely limited. There are numerous Nostr address services like Primal, both paid and unpaid, most of which have no terms and conditions or terms of service, or have vague clauses with no protective effect (… we reserve the right …). Even more problematic is the fact that information about the company’s registered office and place of jurisdiction is often missing, which makes the risk of shutdown incalculable (it is better to avoid providers from Australia, Canada, the UK, the EU, and, after the Baud case, Switzerland).
PS: For owners of their own internet domains, there is a secure option; more on this in Part 2.
Content
Since certain Nostr content is stored redundantly on different relays (servers), it is considered unchangeable and indelible, and therefore effectively uncensorable. Selecting suitable relays is a prerequisite for this and is the responsibility of the authors. The following content can be considered uncensorable
Chats
Blogs
Comments
Reactions (likes, reposts, bookmarks)
Zaps (donations in sats)
The social graph (followers, follows)
Identity (with the exception of Nostr name and wallet name)
All media data should be considered unsafe per se.
Images
All sources with a locator (URL) are unsafe, especially silos such as LinkedIn, Facebook, Instagram, X, etc.
All sources with an identifier (URI) are safer, according to the Nostr standards Blossom and Route96, such as Primal
(this concept becomes very secure when this data is stored redundantly on multiple media stores → via auto-sync)
Audio (podcasts)
almost all are insecure, as they are predominantly linked to a host via URL, e.g. Soundcloud Radio München
Video
similar to audio, except that authors follow the monopolist YouTube and unfortunately do not make sufficient use of alternatives, which increasingly leads to such results
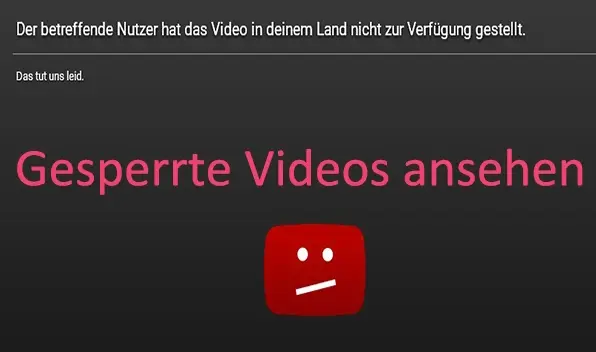
Ms. Fenigson also uses YouTube to commercialize her content, but she also uses numerous additional or parallel channels on Primal
Therefore, in the event of an attack on them, their chats and articles on Nostr would still be accessible, as would the beautiful vacation photos from around the world, and the videos on Primal (unless the attack comes from Primal or affects them).
This brings us to the attack vectors, which form the basis of any security concept (type of attack, probability, impact assessment, prevention costs). These can essentially be divided into three categories, which would take too long to describe in detail here.
technical
organizational → from within
legal → through Five Eyes, EU (also in Switzerland) - Baud case
Security is primarily a question of mindset and begins with the fundamental realization: “Don’t trust - verify!”
Nostr offers decentralization and redundancy as a design principle to increase resilience, but not completely (media data).
For further optimization, the authors themselves are required to develop individual analyses and solutions.
In the case of Ms. Fenigson, I would see the simultaneous use of media storage and name service at Primal as a cluster risk (single point of failure); for an activist with her reach, her own domain would be appropriate.
So the question is not how censorable Nostr is, but how censorable AM I on Nostr? And with this realization, as well as individual demands for censorship resistance, the necessary measures to achieve this become apparent.
Self-determination is based on personal responsibility!